Hack Networks & Devices Right from Your Wrist with the Wi-Fi Deauther Watch
The Deauther Watch by Travis Lin is the physical manifestation of the Wi-Fi Deauther project by Spacehuhn, and it's designed to let you operate the Deauther project right from your wrist without needing a computer. That's pretty cool if you want to do all the interesting things that the Wi-Fi Deauther can do without plugging it into a device.
If you missed our guide on using an ESP8266-based Wi-Fi Deauther, you might be confused about what the Deauther does. For one, it can create deauthentication and disassociation packets, which can kick devices off the same Wi-Fi network the Deauther is attacking. It can do this over and over again, constantly jamming the network so that devices can't connect or stay connected.
Wi-Fi security cameras are an interesting use-case for this type of attack. You could use the Deauther Watch wearable hacking tool, then hunt down the Wi-Fi network that a security camera you come across is connected to, then send out a deauth attack to kick the cameras off the network so you can skate by unnoticed.
The Wi-Fi Deauther project can scan for both nearby access points and connected devices, and it can even clone any Wi-Fi network it sees. It can also generate dozens of fake Wi-Fi networks with any names you want, monitor channels for packet traffic between devices, and do all of this from a fancy built-in interface.
What You'll Need:
Now, you can actually build a Deauther Watch yourself if you want to buy all the components separately, but I recommend checking out one of the links below to pick a pre-flashed one up with all the parts included.
Step 1Flash from Scratch (If Needed)
The Deauther Watch should come pre-flashed with the right firmware, but if it's missing the software, has corrupted software, or something's not working right, you can install or reinstall it. In any of those cases, make sure you have the esptool installed with:
Next, go to the Releases page of Spacehuhn's Wi-Fi Deauther project on GitHub to make sure you're getting the most recent firmware version. Find and download the BIN file for the most recent Deauther Watch, which is currently one of these:
If you have any problems installing the firmware, Spacehuhn's Wi-Fi Deauther Wiki on GitHub is a great resource to find the commands needed and some tips and tricks for installing the BIN file on the Watch.
Plug in the ESP8266 microcontroller on the Deauther Watch to your computer using a Micro-USB cable, then locate the port that it's connected to. To do that, use ls /dev/cu.* on macOS, dmesg | grep tty on Linux, or by looking in the Device Manager for the com port in Windows. We have many microcontroller guides that show locating the port in more detail, so check one of those out if you have any issues.
When you've got the right port, flash the firmware using the following command. Make sure to replace /dev/ttyUSB0 with the port your Deauther Wristband is connected to, and change the BIN file name if it's not the same version.
This should write the firmware to the device, but the screen may not turn on.
Step 2Enable the Screen (If Needed)
If your Deauther Watch's screen isn't working, then you'll need to enable it. The Wi-Fi Deauther Wiki has a good Setup Display and Buttons resource if you need it at any point.
With your Deauther Watch still connected to your computer via Micro-USB cable, connect to it using screen with the following command. You'll need to replace the port with the one your Deauther Watch is connected to.
Alternatively, you can connect to it in Arduino IDE. If you want to go that route, open Arduino IDE, click "Tools" in the menu, select "Port," and choose the port of your connected Deauther Watch. Then, press Command-Shift-M on your keyboard or click on the serial monitor button in the current window to open the serial monitor
Once connected, either through a terminal or Arduino IDE, type help to see a list of commands and confirm you're connected properly. You should see output like below.
Now, run the following commands in your terminal or Arduino IDE to enable the screen.
You may need to restart the device for the settings to take effect. When you boot back up, the screen should now be working!
Step 3Create a Reactive Target (Optional)
To have something legal to practice on, it's good to create a reactive target, which is basically a device on a Wi-Fi hacking test network. One can be made based on the default Arduino IDE "WiFiAccessPoint" sketch for ESP8266-based microcontrollers like the D1 Mini.
Kody Kinzie has a modified sketch on his WiFiHackingWorkshop project on GitHub. The sketch is the ReactiveTarget.ino file, so make sure that's the one you grab. Download that, then flash it over to your ESP8266. The code box below shows the ReactiveTarget.ino file contents if you want to rebuild it yourself.
If you need help with this, check out my previous guide on playing Wi-Fi hacking games legally using microcontrollers, which shows a similar step.
This sketch continually checks to see if a Wi-Fi network is accessible, if the device can connect successfully to it, or if it's being blocked. If it's being blocked, then the ESP8266 will go ahead and warn me with a red flash, and if it's able to connect successfully, it'll let me know with a green flash. If it's never able to connect at all, meaning something's wrong with my access point, the ESP8266 will flash blue.
Step 4Scan for Target Networks
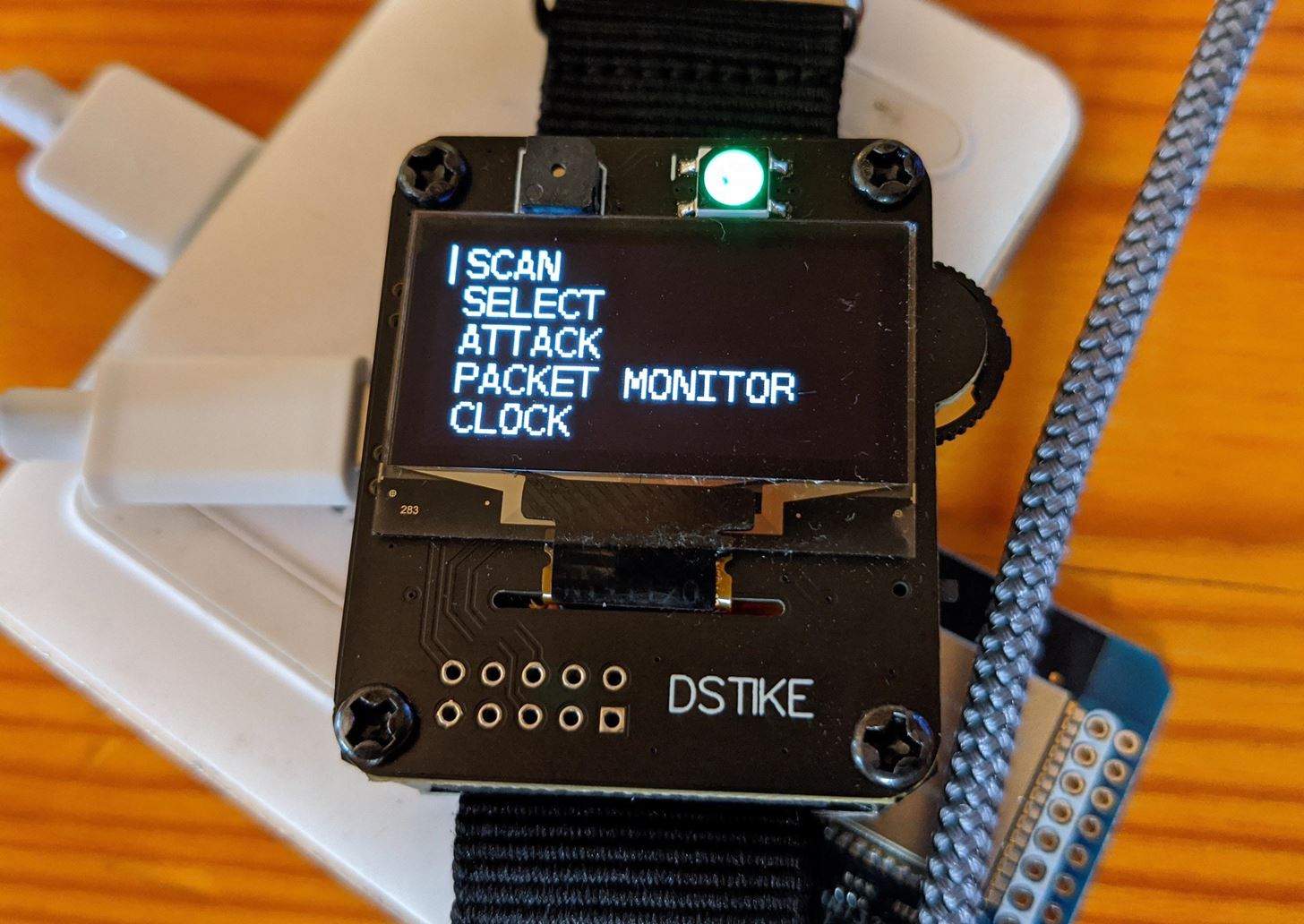
Now, we can turn on the Deauther Watch by flipping the switch on the side. From the main watch menu, use the scroll switch to select the SCAN option, then press the scroll switch to enter the scan menu.
From the scan menu, you can decide to scan for access points (SCAN APs), stations (SCAN STATIONS), or both (SCAN AP + ST). After you decide which to scan for and have selected it with the scroll switch, press the scroll switch to begin the scan.
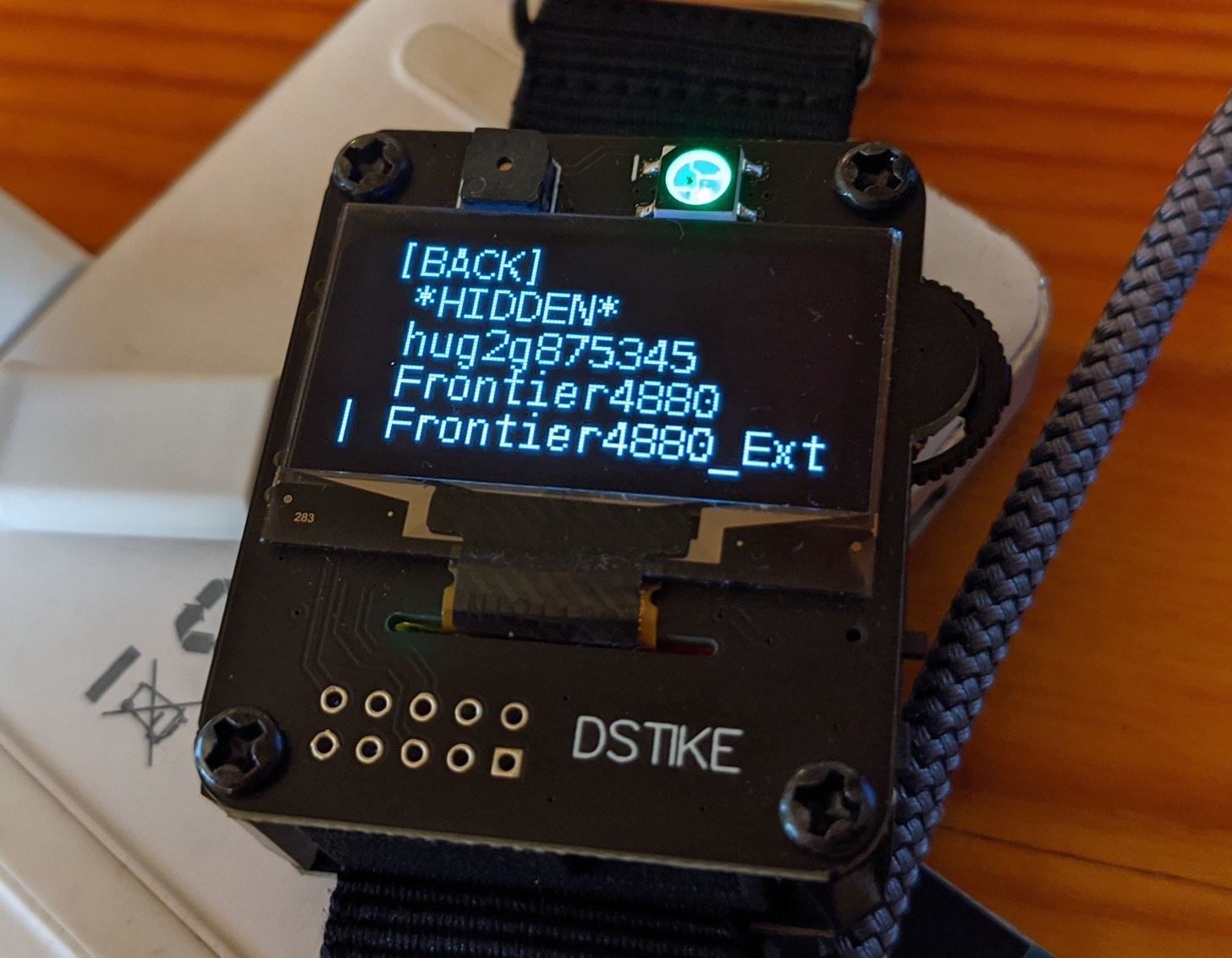
After the scan is complete, it will show you how many APs, stations, or both were found. Now, go back to the main menu and open the SELECT menu. Here, you can see APs or stations that were detected by the scan.
Next, go through the APs, Stations, Names, and SSIDs options until you find your reactive target. Select your target, and press the scroll wheel to mark the target with an asterisk (*) and save it to the target list.
Step 5Attack a Targeted Network
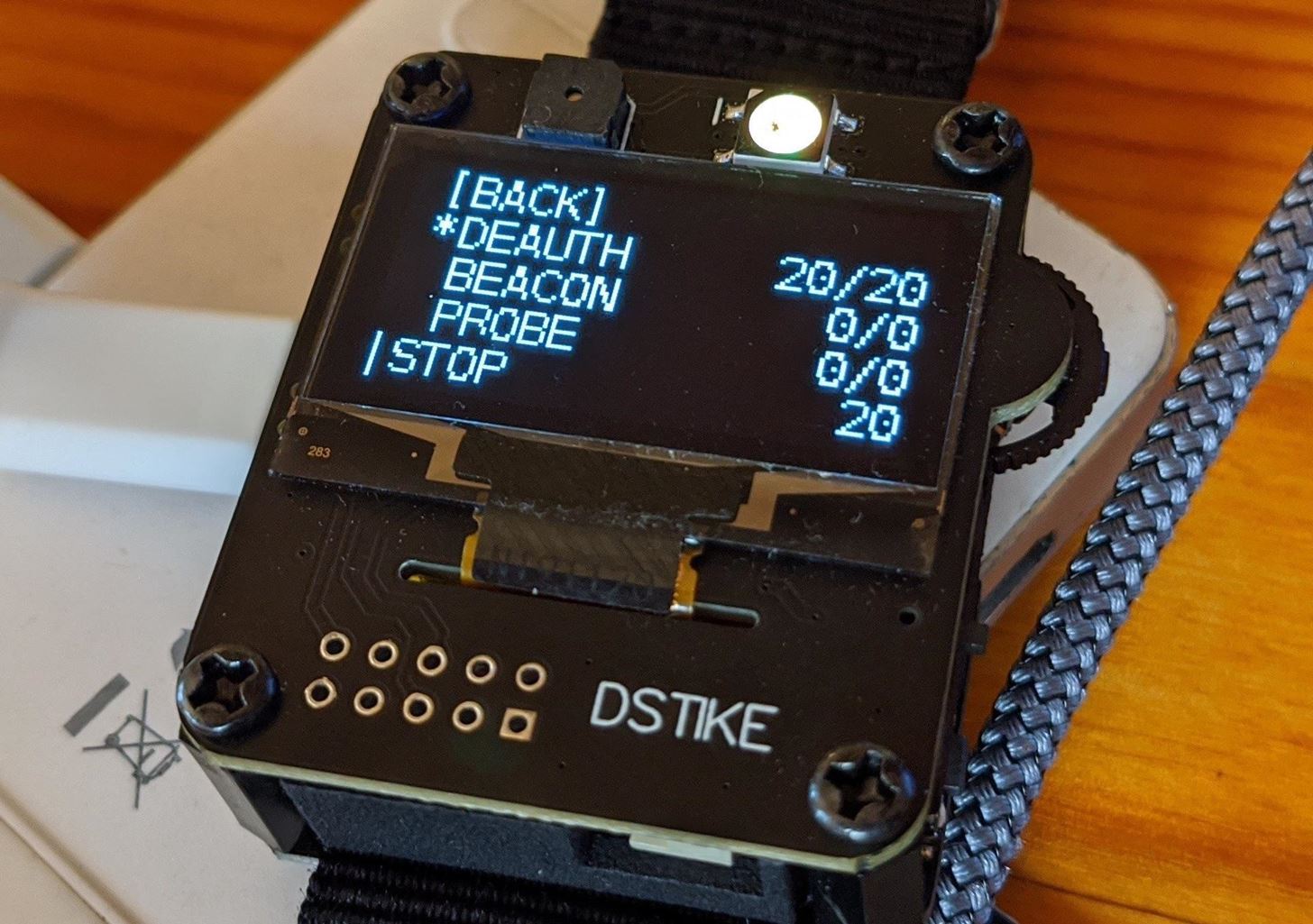
Go back to the main menu and select the ATTACK menu item this time. Once there, you'll have the option to use the DEAUTH, BEACON, or PROBE attacks.
If you want to clone this over and over, you could use the beacon attack. If I want to send out a bunch of probe frames looking for this network or device, try the probe attack.
I'm going to select the deauth attack. Select DEAUTH, then go down to START and press the button to begin. This should disconnect the target from its network, and the ESP8266 reactive target should start blinking red in distress.
You should be successfully jamming the Wi-Fi of the target, and the reactive target should no longer connect to the Wi-Fi network. Once you're ready to stop, you can press the scroll button again to stop the attack, and the reactive target can join the network again.
This was just a quick little demonstration of how you can use the Deauther Watch to scan, select, and attack a network. To start attacking the device again, just start the attack again.
Play Safe with Your Deauther Watch
The Deauther Watch is a really amazing project and a great way to support the developers of the Wi-Fi Deauther project. If you want to pick one of these watches up, keep in mind that it can do some things that might be illegal in your country or region, like hacking a Wi-Fi network that you don't have permission to attack. That could be a serious problem, so make sure you check your local laws before you start firing off this device on networks you don't have permission to test.
Copyright Disclaimer under section 107 of the Copyright Act 1976, allowance is made for “fair use” for purposes such as criticism, comment, news reporting, teaching, scholarship, education and research.
Fair use is a use permitted by copyright statute that might otherwise be infringing.
Non-profit, educational or personal use tips the balance in favor of fair use.
One of the rights accorded to the owner of copyright is the right to reproduce or to authorize others to reproduce the work in copies or phonorecords. This right is subject to certain limitations found in sections 107 through 118 of the copyright law (title 17, U.S. Code). One of the more important limitations is the doctrine of “fair use”. The doctrine of fair use has developed through a substantial number of court decisions over the years and has been codified in section 107 of the copyright law.
Section 107 contains a list of the various purposes for which the reproduction of a particular work may be considered fair, such as criticism, comment, news reporting, teaching, scholarship, and research. Section 107 also sets out in four factors to be considered in determining whether or not a particular use is fair:
1. The purpose and character of the use, including whether such use is of commercial nature or is for nonprofit educational purposes
2. The nature of the copyrighted work
3. The amount and substantiality of the portion used in relation to the copyrighted work as a whole
4. The effect of the use upon the potential market for, or value of, the copyrighted work
The distinction between fair use and infringement may be unclear and not easily defined. There is no specific number of words, lines, or notes that may safely be taken without permission. Acknowledging the source of the copyrighted material does not substitute for obtaining permission.
The 1961 Report of the Register of Copyrights on the General Revision of the U.S. Copyright Law cites examples of activities that courts have regarded as fair use: “quotation of excerpts in a review or criticism for purposes of illustration or comment; quotation of short passages in a scholarly or technical work, for illustration or clarification of the author’s observations; use in a parody of some of the content of the work parodied; summary of an address or article, with brief quotations, in a news report; reproduction by a library of a portion of a work to replace part of a damaged copy; reproduction by a teacher or student of a small part of a work to illustrate a lesson; reproduction of a work in legislative or judicial proceedings or reports; incidental and fortuitous reproduction, in a newsreel or broadcast, of a work located in the scene of an event being reported.”
Copyright protects the particular way an author has expressed himself. It does not extend to any ideas, systems, or factual information conveyed in the work.
The safest course is always to get permission from the copyright owner before using copyrighted material. The Copyright Office cannot give this permission.
When it is impracticable to obtain permission, use of copyrighted material should be avoided unless the doctrine of fair use would clearly apply to the situation. The Copyright Office can neither determine if a certain use may be considered fair nor advise on possible copyright violations. If there is any doubt, it is advisable to consult an attorney.
FL-102, Revised September 2010



Comments
Post a Comment